What is the difference between public and private subnets?
Understand the key differences between public and private subnets in AWS networking. Learn how they function, when to use them, and why they matter.

In the world of cloud computing, particularly with Amazon Web Services (AWS), understanding the networking architecture is vital for building secure and scalable applications. One of the foundational concepts in AWS networking is the distinction between public and private subnets.
A subnet, short for sub-network, is a segmented piece of a larger network. In AWS, subnets exist within a Virtual Private Cloud (VPC), which allows users to isolate and control cloud resources. The categorization of subnets into "public" and "private" is determined by how resources within those subnets interact with the internet.
Lets explore the core differences between public and private subnets, how theyre used, and why understanding them is essentialespecially for anyone pursuing an AWS Course in Pune or similar cloud-based learning path.
What is a Public Subnet?
A public subnet is one that is directly accessible from the internet. Instances launched in a public subnet can communicate with the internet, provided they have an Elastic IP (EIP) or a public IP address and the appropriate route configured.
Public subnets typically host:
-
Web servers
-
Bastion hosts
-
Load balancers
-
Any component that needs direct internet access
To qualify as a public subnet in AWS:
-
The subnet must be associated with a route table that has a route pointing to an Internet Gateway (IGW).
-
The instances in the subnet must have public IPs assigned.
This setup allows incoming traffic (like HTTP/HTTPS requests) to reach the hosted resources, making public subnets essential for customer-facing applications.
What is a Private Subnet?
A private subnet, by contrast, does not have direct internet access. The instances within these subnets cannot be reached from the internet, nor can they directly initiate outbound connections to the internet without a NAT (Network Address Translation) gateway or instance.
Private subnets are used for hosting:
-
Application servers
-
Databases
-
Internal APIs
-
Backend logic and services
This added layer of isolation improves security and protects sensitive resources from external exposure.
To access the internet from a private subnet, traffic is routed through a NAT gateway, which resides in a public subnet. This allows instances in private subnets to download patches or connect to AWS services securely without exposing themselves to the open internet.
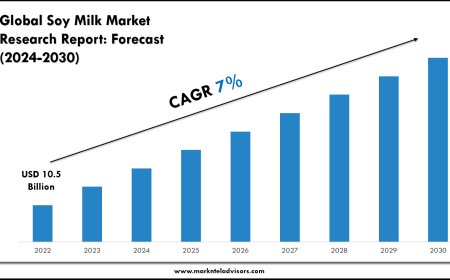
Key Differences Between Public and Private Subnets
| Feature | Public Subnet | Private Subnet |
|---|---|---|
| Internet Access | Yes, via Internet Gateway | No direct access; uses NAT Gateway |
| Public IP Assignment | Required for internet access | Not required |
| Use Cases | Frontend applications, web servers, NAT Gateways | Databases, application servers, background services |
| Exposure | Accessible from outside the VPC | Isolated from public internet |
| Route Table | Includes route to Internet Gateway | Includes route to NAT Gateway (if needed) |
Understanding these differences is critical for professionals managing secure and scalable cloud environments. This knowledge is foundational for anyone considering enrolling in AWS Training in Pune or seeking to specialize in cloud infrastructure.
When to Use Public vs. Private Subnets
Choosing between public and private subnets depends on your application architecture and security requirements.
Use public subnets when:
-
Resources need to be directly accessible from the internet (e.g., web servers).
-
You're hosting a NAT Gateway for private subnet access.
Use private subnets when:
-
You want to keep sensitive data secure (e.g., databases).
-
Resources dont need to be exposed to the internet directly.
A common architecture pattern is the "three-tier architecture," which includes public subnets for load balancers, private subnets for app servers, and another set of private subnets for databases.
Best Practices for Subnet Design in AWS
-
Design your VPC with at least two Availability Zones for high availability.
-
Use public subnets only for resources that require direct internet access.
-
Place your NAT Gateway in a public subnet and ensure private subnets route through it.
-
Avoid assigning public IPs to instances in private subnets.
-
Use security groups and Network ACLs to control traffic flow.
These practices are emphasized in hands-on labs and real-world scenarios in most structured AWS Classes in Pune and similar courses designed to prepare professionals for industry demands.
Final Thoughts
Understanding the difference between public and private subnets in AWS is crucial for anyone involved in cloud architecture, DevOps, or cybersecurity. Whether you're deploying a simple web app or architecting a multi-tier enterprise solution, correctly configuring your subnets ensures performance, scalability, andmost importantlysecurity.
If you are new to cloud computing or looking to build a strong foundational knowledge, consider joining an AWS Course in Pune. These programs often blend theoretical learning with hands-on labs that cover real-world scenariosincluding subnet configuration, VPC setup, and more.
For a broader look at AWS and its suite of services, check out our related blog:
? What are Amazon Web Services